
Part III – Until the focus expands to data protection – Taking action
This is the thrid of a three-part series (read part II here) about how vendors are keeping backup alive, however what they can and should do to shift and expand the conversation to data protection and related themes.
Modernizing is more than simply swapping one technology for another
As I have said for a couple of years now, modernizing data protection, or data protection modernization if you prefer is more than simply deduping or swapping out media, mediums, tape, disk, clouds, software or services like a recurring flat tire on an automobile. If you keep getting flat tires, instead of treating the symptom, find and fix the problem which means for backup, taking a step back and realizing that what is really being done is protecting data (e.g. data protection).
Granted the security people may not like sharing the term data protection as some of them prefer to keep that unique, just like some of the compliance people want to keep archiving exclusive to their focus areas, however lets move on.
On the other hand, data protection also means that, protect, preserve and enable data and information to be accessed and served when and were needed in a cost-effective way with consistency and coherency.
Sure there is still the act of making a copy or a backup at time intervals (frequency) with various coverage (how much gets copied) to multiple locations (copies) with versions kept for different amounts of time (retention) to support RTO and RPO, not to mention SLA and SLO for ITSM (how’s that for some buzzword bingo ;).

This means using copies, sync (or rsync), snapshots, replication and CDP, discrete copies such as backups along with all the other buzzword bingo enabling tools, technologies and techniques (e.g. Agent or Agent less, Archive, Availability zones. Not to mention Bare metal, virtual bare metal, Block based, CDP, Compression, Consolidation, Deletion, Data management, Dedupe, eDiscovery, durability, erasure coding/parity, file level, meta data and policy management, replication, snapshots, RAID, plugin, object storage, NAS, VTL, disk, tape, cloud, virtual among others). In addition to taking a step back, this also means rethinking why, how, when, where data (and information) gets protected to meet various threat risks as well as diverse business requirements.

No tools in the toolbox (physical, virtual or cloud)
Part of the rethinking is expanding the focus from what are the tools, who makes what’s, how do they work, their features and functions to how to use the tool or technology for different things.

Various tools (hardware, software, services) for different physical, virtual and cloud tasks
This is like going into a store like Lowe’s or Home Depot and talking to the sales people their (ok, associates or team members) who can tell you everything thing there is to know about the tool or technology, however they can’t tell you how to use it.
Sometimes you can get lucky and there will be somebody working at the tool (hardware or software) store who will ask you what you are trying to do and give you advice based on their experience of a different approach with another tool or tools and some supporting material or parts and supplies.
Does this sound familiar to data infrastructure or IT in general, not to mention server, storage, backup and data protection among other areas of interest?
If all you have, or know how to use is a hammer, then everything or situation starts to look like a nail. Expand your toolbox with more tools AND learn how to use or apply them in new and different ways. Align the right tool, technology and technique to the task at hand! |
Expand from talking new technology to using new (and old) things in new ways
In addition to focusing on new tools and technology along with their associated terminologies across physical, virtual and cloud environments, it is also time to expand the discussion and awareness to using new (and old) things in new ways. This also means expanding the terminology from backup/restore to more comprehensive data protection as part of modernizing your environment.
For example some people (and vendors) use the term or phrase "Modernizing Data Protection" to mean swap out tape for disk, or disk for cloud, or one cloud for another cloud, or upgrade from one software version to another, or simply swap one vendors software or tool for another, yet continue to use it for all practical purposes in the same way.
Sure, moving from hourly or daily copies to tape over to direct to disk and then either redeploying tape where it is better suited (streaming large amounts of data, powering off to save energy, e.g. deep cold archive). This also means leveraging fast random access to small files that need to be recovered (usually within first hours or days of being protected).
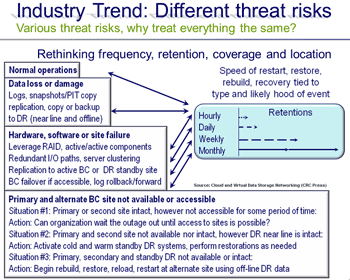
Aligning tools, technologies, techniques to various threat risk scenarios
Modernizing data protection (also known as transformation) also means recognizing that not everything is the same in the data center or information factory regardless of size, and that there are also different and evolving data access patterns. Another reason and trend to consider is that there is no such thing as an information recession and that people plus data are living longer as well as getting larger.
Expand your awareness and focus beyond simply knowing what the tools are and who makes them to how, when, where, why along with pros/cons of using them to discuss different situations. This means having multiple tools in your data protection toolbox as well as knowing how to use different tools for various tasks instead of always using a hammer. – GS @StorageIO |
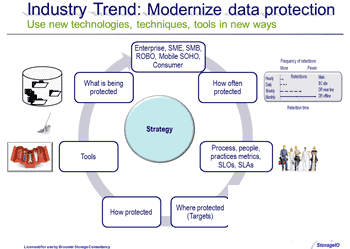
The data protection continuum, more than tools and technoligiues
Call to action, stop talking about it, start walking the talk
If you or somebody else is tired of hearing about backup, then stop complaining about it and take some action. Following are some things to expand your thinking, awareness, discussions and activities around modernizing data protection (and moving beyond traditional backup).
- Take a step back and check the basics or fundamentals of data protection which when enabled, allows your organization to move forward after a small or big incident (or disaster).
- Start thinking beyond backup tools and technologies (hardware, software, services) particular how its been done, to why it needs to be done, how can it be done differently.
- Revisit why you are protecting different things, realize that not everything is the same, so does that mean you have to protect everything the same way?
- Learn about how to use different tools and technologies which is different from learning about the tools, features and functions.
- Also keep in mind that a barrier is often people and process (along with organizational politics) that also result in new (and old) technologies being used in old ways.
- Think about using different tools and technologies in different e.g. hybrid ways.
- This means start using new (and old) tools, techniques, techniques in new ways, start to apply your return on innovation by using things to discuss issues, vs. simply using them for the sake of using them.
In addition to the above items, here are some added links on various topics and themes mentioned here:
BackupU – Vendor and technology neutral series of on-line webinars, Google+ hangouts, book chapter downloads and other content (Sponsored by Dell Data Protection Software, that’s a disclosure btw )
Via StorageIOblog – Only You Can Prevent Cloud Data Loss,
Cloud conversations: confidence, certainty and confidentiality,
Modernizing data protection with certainty,
More Data Footprint Reduction (DFR) Material,
More modernizing data protection, virtualization and clouds with certainty,
EMC Evolves Enterprise Data Protection with Enhancements and Data protection modernization, more than swapping out media.
Via StorageIO Reports/Resources Page – backup, restore, BC, DR and archiving available here including presentations and book chapter downloads
Via Internet evolution – People, Not Tech, Prevent IT Convergence.
Closing comments (for now)
Now having said all of that, It would be unrealistic to think that we can simply overnight drop the term backup and switch to data protection, after all, we need backwards compatibility. However until the industry which means from vendors, their pundits (analyst, bloggers, consultants, evangelists), press/media, vars, investors and customers start thinking and speaking in the broader context of data protection, life beyond backup, guess what, we will still be talking about backup. Start calling it (e.g. backup) data protection and perhaps within a generation (or sooner), the term backup will have been ILM, compressed, deduped, tiered, spun down, put into deep cold archive storage to take a long REST on object storage with a NAS interface in a software defined hybrid virtualized cloud ;).
Watch for more data protection conversations about related trends, themes, technologies, techniques perspectives in my ongoing data protection diaries discussions (e.g. www.storageioblog.com/data-protection-diaries-main/).
Ok, nuff said
Cheers
Gs
Greg Schulz – Author Cloud and Virtual Data Storage Networking (CRC Press), The Green and Virtual Data Center (CRC Press) and Resilient Storage Networks (Elsevier)
twitter @storageio
All Comments, (C) and (TM) belong to their owners/posters, Other content (C) Copyright 2006-2026 Server StorageIO and UnlimitedIO LLC All Rights Reserved
![]()

